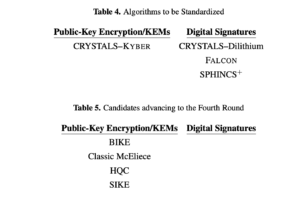
Fault-tolerant quantum computers won’t exist for years – a decade is the most common estimate. When they do arrive, thanks to Shor’s now-famous algorithm, they will be able to crack the most widely-used encryption methods, which are based on factoring. Earlier this month, the National Institute of Standards and Technology (NIST) settled on four algorithms – one for public-key-encryption (KEM) and three for digital signatures – based on lattice problems and hash functions, for incorporation into new post-quantum encryption standards.
These are deliverables of NIST’s post-quantum cryptography standardization project (PQC), begun in 2016 and involving multiple rounds of submissions by industry, academia, and public entities, and assessment by NIST. This was the third round. A final fourth round is planned to consider four more algorithms.
NIST has issued a thorough report detailing the PQC process and sharing, for example, benchmark data across multiple processor types, and explaining NIST’s rationale for the selections. Three selection criteria were used: 1) security (most important), 2) cost and performance, and 3) algorithm and implementation characteristics. The latest NIST report isn’t news in the sense that the quantum community and virtually all enterprise data security professionals have been closely tracking NIST’s PQC efforts.
Even as NIST works to formalizes the new standards, it has begun a new project – Migration to Post Quantum Cryptography – in collaboration with industry to develop tools and migration practices to protect data. That project is being run by NIST’s National Cybersecurity Center of Excellence (NCCoE). Here’s a snapshot of the program’s main goals:
- Demonstrate the use of automated discovery tools to identify instances of quantum-vulnerable public-key algorithm use, where they are used in dependent systems, and for what purposes.
- Once the public-key cryptography components and associated assets in the enterprise are identified, the next project element is prioritizing those applications that need to be considered first in migration planning.
- Finally, the project will describe systematic approaches for migrating from vulnerable algorithms to quantum-resistant algorithms across different types of organizations, assets, and supporting technologies.
You can read the rest of the story at HPCwire.
The post The Race to Ensure Post Quantum Data Security appeared first on Datanami.


0 Commentaires